petep
May 4, 2025, 11:15am
1
Hi!
I’ve observed some strange behaviour and I’d like to understand this a little better.
Jami is sending malformed DNS requests to 58.249.126.8
inetnum: 58.249.0.0 - 58.249.127.255
The requests looks like this:
1 12:00:55.099048962 10.0.0.1 → 58.249.126.8 DNS 123 Unknown operation (12) 0x85a1[Malformed Packet]
Anyone know what’s happening here?
Jami is on Rocky 9
Regards,
P.
Hmm, what is your default DNS server address?
petep
May 4, 2025, 4:12pm
3
I can confirm that this IP doesn’t appear in my /etc/resolv.conf as a nameserver. All other applications use the NS hosts which are listed there. Only Jami is connecting to this IP address which I have not heard of before.
1 Like
petep
May 9, 2025, 2:03pm
5
Caveat: I’m not a developer
I have done a dump of the packets but it isn’t plain text. The only recognisable strings I can see are:
Does this sound typical of a OpenDHT packet?
Thanks.
1 Like
Probably, I also found them in parsed_message.h of OpenDHT (Jami used this library).
/*
* Copyright (C) 2014-2023 Savoir-faire Linux Inc.
* Author(s) : Adrien Béraud <adrien.beraud@savoirfairelinux.com>
*
* This program is free software; you can redistribute it and/or modify
* it under the terms of the GNU General Public License as published by
* the Free Software Foundation; either version 3 of the License, or
* (at your option) any later version.
*
* This program is distributed in the hope that it will be useful,
* but WITHOUT ANY WARRANTY; without even the implied warranty of
* MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
* GNU General Public License for more details.
*
* You should have received a copy of the GNU General Public License
* along with this program. If not, see <https://www.gnu.org/licenses/>.
*/
#pragma once
#include "infohash.h"
show original
Do you mind parsing those packets with the demo page of msgpack-lite ?
1 Like
hkk
May 9, 2025, 8:20pm
7
If it’s a dht node then don’t worry too much about it
2 Likes
petep
May 10, 2025, 11:17am
8
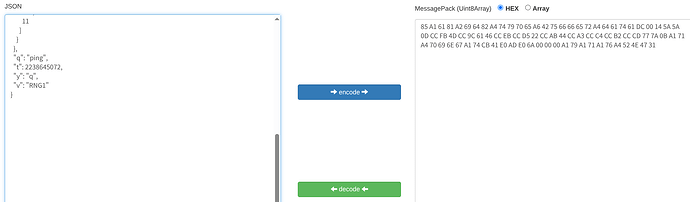
Good call on parsed_message.h . That’s convincing evidence for the DHT case. However I was unable to get the packets to deserialise using the msgpack demo. This implies one of two things:
They’re not OpenDHT packets
I didn’t do it right!
Mmmm..
My bad.
Sorry.
petep
May 11, 2025, 12:08pm
10
Now I’m getting somewhere. The request (not reply) from my machine running Jami looks like this:
{
and something else that might be significant, the requests take place exactly every 10 minutes.
Is this OpenDHT?
Thanks.
Yes, and it’s a request to find node.
petep
May 11, 2025, 3:36pm
12
Thanks Rubus. Good to have that confirmation. I can rest easy now!
Thanks again for your help.